South Korea’s financial industry has come under intense cyber pressure following the discovery of a large-scale ransomware campaign linked to the Qilin ransomware operation. Security researchers say the attacks were not isolated incidents but part of a coordinated supply chain compromise that enabled threat actors to infiltrate multiple organizations simultaneously.
Unlike traditional ransomware intrusions, this campaign leveraged a Managed Service Provider (MSP) as the initial entry point, allowing attackers to spread laterally across dozens of financial entities. The operation highlights the growing risks associated with third-party access and supply chain dependencies in modern enterprise environments.
With confirmed data theft, politically charged messaging, and possible ties to state-sponsored threat actors, the incident underscores how ransomware attacks are increasingly blending cybercrime with geopolitical objectives.
Qilin Ransomware and the Supply Chain Attack Model
According to an in-depth analysis by Bitdefender, the campaign combined the operational scale of the Qilin Ransomware-as-a-Service (RaaS) platform with tactics commonly associated with advanced persistent threat (APT) groups. The attackers reportedly gained initial access by compromising a single upstream MSP, which provided IT services to multiple financial organizations in South Korea.
By abusing trusted vendor access, the attackers were able to deploy ransomware across numerous networks without needing to individually breach each target. This approach significantly reduces effort while maximizing impact, making MSPs highly attractive targets for modern ransomware groups.
Supply chain attacks of this nature are particularly dangerous because they exploit implicit trust relationships, often bypassing perimeter defenses and traditional detection mechanisms.
Sharp Rise in Ransomware Victims in South Korea
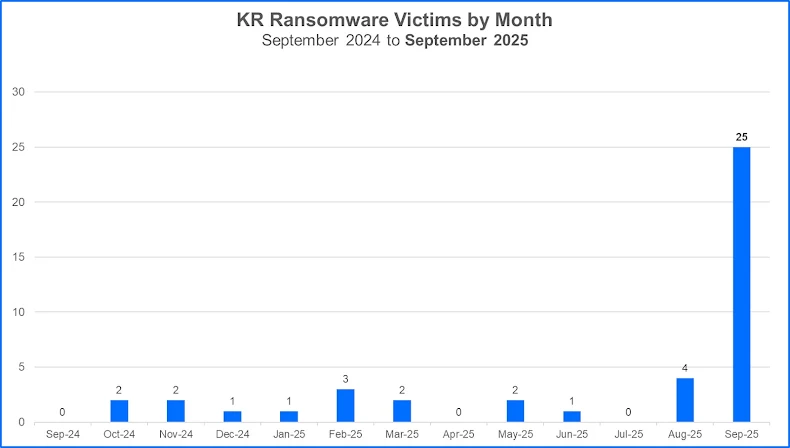
Bitdefender began investigating the campaign after identifying an unusual surge in ransomware victims located in South Korea during September 2025. That month, the country became the second-most targeted nation globally, trailing only the United States.
Data showed 25 confirmed ransomware incidents in South Korea for September alone—a dramatic increase compared to the historical average of roughly two cases per month observed between September 2024 and August 2025. Even more striking was the fact that all 25 incidents were attributed exclusively to the Qilin ransomware group.
Of these victims, 24 organizations operated within the financial sector, pointing to a highly focused and deliberate targeting strategy rather than opportunistic attacks.
“Korean Leaks” Campaign and Targeted Industries
The attackers labeled the campaign “Korean Leaks,” a name that reflected both the scale of data theft and the narrative used to justify the attacks. Over the course of the operation, data from 28 confirmed victims was stolen, totaling more than one million files and approximately 2 terabytes of sensitive information.
Interestingly, posts related to four additional victims were later removed from Qilin’s data leak site. Researchers believe this could indicate successful ransom negotiations, takedown requests, or internal decisions made by the attackers regarding disclosure.
The overwhelming focus on asset management firms, financial institutions, and investment-related organizations suggests a strategic effort to disrupt South Korea’s financial ecosystem.
Timeline of the Attack Waves
The Korean Leaks campaign unfolded in three distinct publication waves, each marked by escalating pressure tactics and evolving messaging:
- Wave One (September 14, 2025):
Included 10 victims primarily from the financial management sector. - Wave Two (September 17–19, 2025):
Featured nine additional victims and intensified public messaging. - Wave Three (September 28–October 4, 2025):
Added nine more victims and shifted toward traditional ransom-driven extortion language.
This structured release strategy demonstrates careful planning and a desire to control public narrative while maintaining pressure on victims.
Propaganda and Political Messaging as an Extortion Tool
One of the most unusual aspects of the campaign was its heavy reliance on political rhetoric and propaganda, especially during the early stages. Rather than focusing solely on financial extortion, the attackers framed their actions as a public service.
In the first wave, the group claimed the stolen data could expose alleged stock market manipulation and corruption involving high-profile politicians and business leaders. They presented themselves as whistleblowers rather than cybercriminals, a tactic rarely seen in conventional ransomware operations.
Subsequent waves escalated the narrative, warning that releasing the data could destabilize South Korea’s financial markets and urging authorities to investigate the affected organizations under strict national data protection laws.
Shift Back to Financial Extortion
By the third wave, the tone of the campaign changed noticeably. While earlier messaging emphasized political motives and systemic corruption, later posts adopted language more consistent with Qilin’s typical profit-driven extortion tactics.
Security researchers believe this shift indicates deeper involvement from Qilin’s core operators, who are known to prioritize ransom payments over ideological messaging. The transition suggests that while affiliates may influence narrative direction, the ransomware group ultimately maintains control over final disclosures.
Bitdefender noted that grammatical patterns and stylistic inconsistencies in the posts closely matched previous Qilin communications.
Possible Links to North Korean Threat Actors
Although Qilin is widely believed to be a Russia-linked ransomware operation, the campaign has raised questions about potential involvement from North Korean state-affiliated actors, specifically a group tracked as Moonstone Sleet.
Microsoft previously linked Moonstone Sleet to the deployment of a custom ransomware strain known as FakePenny, which was used in an April 2024 attack against a defense technology company. Earlier this year, researchers observed a shift where the same actor appeared to deliver Qilin ransomware in select cases.
While definitive attribution remains unclear, the strategic targeting of South Korean organizations aligns with North Korea’s broader cyber objectives, including financial disruption and intelligence gathering.
Role of Managed Service Provider Compromise
At the core of the Korean Leaks operation was the compromise of a single MSP. Reports from local media revealed that more than 20 asset management firms were infected after attackers breached GJTec, an IT service provider supporting multiple financial companies.
This incident demonstrates how MSPs can become force multipliers for ransomware campaigns. By infiltrating one trusted provider, attackers can gain privileged access to dozens of downstream clients.
The tactic highlights a critical weakness in many organizations’ cybersecurity strategies: insufficient oversight and security enforcement across third-party vendors.
Why MSPs Are Prime Targets for RaaS Groups
Ransomware-as-a-Service operators increasingly favor MSP compromises because they offer:
- Broad access to multiple victims
- Elevated privileges within client networks
- Reduced need for repeated intrusion efforts
- Higher potential ransom payouts
For threat actors seeking efficiency and scale, exploiting service providers is often more effective than attacking individual organizations directly.






